Configure Site-Specific SAML
Use site-specific SAML in a multi-site environment when you want to enable single sign-on, and you also use multiple SAML identity providers (IdPs) or IdP applications. When you enable site SAML, you can specify the IdP or IdP application for each site, or configure some sites to use SAML and the others to use the default server-wide authentication method.
If you want all server users to use SAML and sign in through the same IdP application, see Configure Server-Wide SAML.
Before you can enable SAML single sign-on at the site level, complete the following requirements:
The Tableau Server identity store must be configured for local identity store.
You cannot configure site-specific SAML if Tableau Server is configured with an external identity store such as Active Directory or OpenLDAP.
Make sure your environment and your IdP meet the general SAML Requirements.
Some features are supported only in server-wide SAML deployments, including but not limited to:
- Password-protected key files, which are not supported in site-specific SAML deployments.
You must configure server-wide SAML before you configure site-specific SAML. You do not need to enable server-wide SAML, but site-specific SAML requires the server-wide configuration. See Configure Server-Wide SAML.
Note the location of the SAML certificate files. You will provide this when you Configure the server to support site-specific SAML.
For more information, see Put metadata and certificate files in place in the topic on configuring server-wide SAML.
Add Tableau Server as a service provider to your IdP. You can find this information in the documentation the IdP provides.
Confirm that the system clocks of the computer hosting the site-SAML IdP and the computer hosting Tableau Server are within 59 seconds of each other. Tableau Serer does not have a configuration option to adjust the response skew (time difference) between the Tableau Server computer and the IdP.
Return URL and entity ID: In the settings for configuring site-specific SAML, Tableau provides a site-specific return URL and entity ID based on these settings. The site-specific return URL and entity ID cannot be modified. These configurations are set by TSM as described in Configure Server-Wide SAML.
Authentication age and response skew: Server-wide settings, maximum authentication age and response skew, do not apply to site-specific SAML. These configurations are hard-coded:
- The maximum authentication age refers to how long an authentication token from the IdP is valid after it is issued. The hard-coded maximum authentication age site-specific SAML is 24 days.
- The response skew is the maximum number of seconds difference between Tableau Server time and the time of the assertion creation (based on the IdP server time) that still allows the message to be processed. The hard-coded site-specific value for this is 59 seconds.
Username: Required. In addition to the server-wide SAML configuration attribute, the site-specific SAML configuration attribute must be set to "username."
Note: For site-specific SAML to operate successfully with a server-wide SAML default, the username attribute configured for server-wide SAML with the wgserver.saml.idpattribute.username configuration key must be "username". The IdP used for server-wide SAML must deliver the username in an attribute named "username."

HTTP POST and HTTP REDIRECT: For site-specific SAML, Tableau Server supports HTTP-POST, HTTP-REDIRECT, and HTTP-POST-SimpleSign.
After you complete the prerequisites listed above, you can run the following commands to configure the server to support site-specific SAML.
Configure Server-Wide SAML. At a minimum, you must run the following TSM command (if you have already configured server-wide SAML, skip to Step 2):
tsm authentication saml configure --idp-entity-id <tableau-server-entity-id> --idp-return-url <tableau-server-return-url> --cert-file <path-to-saml-certificate.crt> --key-file <path-to-saml-keyfile.key>- Enable site SAML. Run the following commands:
tsm authentication sitesaml enabletsm pending-changes apply
About the commands
The sitesaml enable command exposes the Authentication tab on each site’s Settings page in the Tableau Server web UI. After you configure the server to support site SAML, you can continue to Configure SAML for a site to work through the settings on the Authentication tab.
If the pending changes require a server restart, the pending-changes apply command will display a prompt to let you know a restart will occur. This prompt displays even if the server is stopped, but in that case there is no restart. You can suppress the prompt using the --ignore-prompt option, but this does not change the restart behavior. If the changes do not require a restart, the changes are applied without a prompt. For more information, see tsm pending-changes apply.
If you want to review the commands and settings that will be carried out when you run pending-changes apply, you can run the following command first:
tsm pending-changes list --config-only
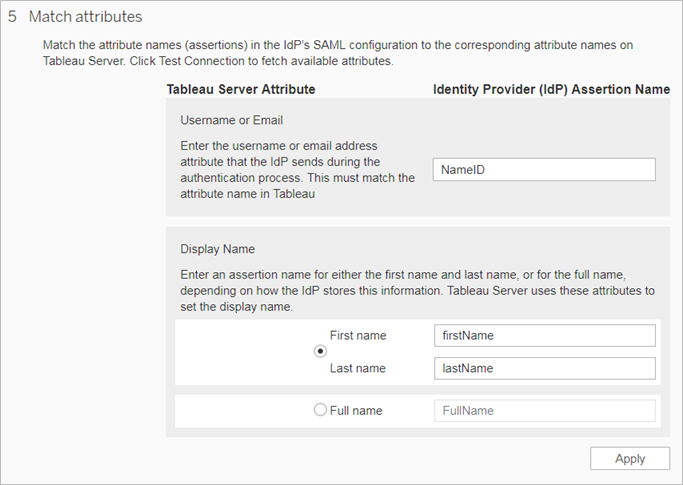
This section takes you through the configuration steps that appear on the Authentication tab in the Tableau Server Settings page.
Note: To complete this process, you will also need the documentation your IdP provides. Look for topics that refer to configuring or defining a service provider for a SAML connection, or adding an application.